Secure Your Entire Microsoft 365 Environment
We provide comprehensive, managed backups to keep your data safe, compliant, and always recoverable.
Core Business Benefits:
Avoid Permanent Data Loss Safeguard your data against user error, malicious attacks, and ransomware. We make data loss a temporary inconvenience, not a permanent catastrophe.

Arconis Cloud to Cloud Backup
Acronis Cloud to Cloud Backup
Complete Coverage Across the M365 Suite
Exchange Online
Protect emails, attachments, contacts, tasks, calendars, and all mailbox types.
SharePoint Online
Secure your sites, collections, documents, and access permission settings.
OneDrive for Business
Safeguard all user files and folders, including their specific access permissions.
Microsoft Teams
Protect entire teams, channels, conversations, files, meetings, and associated team sites
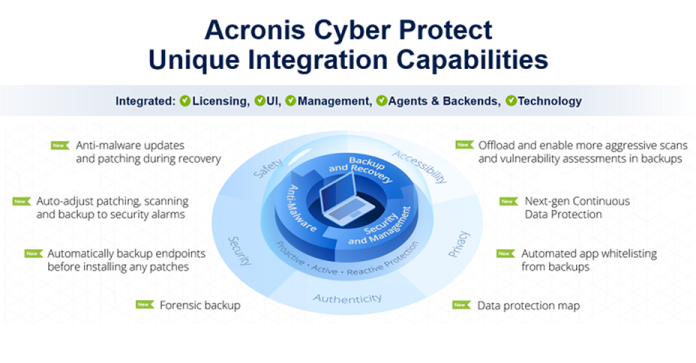
NIS2 requirements & How Acronis can help [1/3]
Risk Management and Аssessment
- The service provider uses the #CyberFit Score to run a report on the security standing of all devices for a client and finds that many of them don’t have disk encryption set up. The service provider then fixes this issue for the client.
- With auto-discovery, the partner identifies and removes rogue devices from the client’s environment.
- Features:
- Global threat monitoring & alerts
- Software & hardware inventory
- Auto discovery of new workloads
- #CyberFit Score
Incident management
- The XDR engine runs for the client’s devices and discovers that a user runs a suspicious script from an unusual geographical location, suggesting an account compromise. The partner suspends the user’s domain account as a remediation step. The script was received by email, and the partners adds the address to the blacklist.
- Features:
- Cyber Security + EDR/XDR
- Email Security
- Threat Hunting (roadmap)
- Forensic backup
Maintenance of Operations
- One of the servers used in the client’s manufacturing process fails, and because the location is far away, it would take a lot of time for the MSP to arrive. The MSP directs someone onsite to just restart the server and press a key, after which the system gets automatically recovered from yesterday’s backup.
- Features:
- One-click recovery
- Continuous backup (CDP)
- Cyber scripting
- Backup Scan
NIS2 requirements & How Acronis can help [2/3]
Emergency Recovery
- The client is a logistics company, with each hour of downtime costing 10k EUR. Their premises are left without electricity and internet connection. The MSP spins up all their production servers from backups in an Acronis cloud in GR1, and users connect to those servers over VPN and keep working.
- Features:
- Disaster Recovery
- Safe Recovery
- Bare Metal Recovery
Supply Chain Security
- The partner is considered to be part of the client’s supply chain and needs to comply with NIS2. Acronis forces the MSP to use MFA and ensures stored data is immutable, so even if someone hijacks the partner’s informational systems, they won’t be able to do anything with the client’s data.
- Features:
- Cyber Security + EDR/XDR
- Email Security
- MFA
- Immutable backups
Vulnerability Management
- Attackers start exploiting a known vulnerability during an attack campaign. Automated patch management ensures that all clients’ workloads are patched within days of patch release by the software vendor.
- Features:
- Vulnerabilities scan
- Automated patch management
NIS2 requirements & How Acronis can help [3/3]
Emergency Communication
- Through Managed Detection and Response (MDR), Acronis provides real-time monitoring, reporting, and integration with client systems, facilitating effective emergency communication as mandated by NIS2. Incidents are immediately remediated, including the use of Disaster Recovery for business continuity. Using the Acronis console, partners have all the details needed to comply with communication requirements.
- Features:
- MDR (Managed Detection and Response)
- Monitoring and reporting
- Integration into customer-specific systems
Cyber hygiene practices and cybersecurity training
- Acronis Security Awareness Training provides essential cybersecurity concepts to non-technical end users, who are often the “weakest link” in cybersecurity defences. The program includes simulated phishing campaigns to strengthen awareness and support compliance with NIS2 requirements.
- Features:
- Security Awareness Training (SAT)
Our Managed Service Features
Partner with us and rest easy knowing a robust, professionally managed solution protects your data.
Automatic Protection
New users, sites, and teams are automatically discovered and backed up.
Granular Restore in Seconds
Quickly recover anything from a single email to an entire SharePoint site.
Powerful Search Capabilities
Instantly find the exact files or communications you need to restore.
Proactive Monitoring & Reporting
Gain full visibility into your backup status with powerful dashboards.
Advanced Security
Your data is protected with multi-level encryption and multi-factor authentication support.
Don’t Leave Your Business Data at Risk
Every day you operate without a true Microsoft 365 backup is a gamble. Let our team assess your current setup and identify and close the gaps that Microsoft leaves open.



